We usually use Netcat to get reverse shell, but from port scanning, file transfer to banner grabbing and exploit, everything is possible with netcat.
In our this detailed guide we will learn why Netcat is called "Hacker's Swiss Army Knife". In our this detailed guide we will learn the uses of Netcat in Kali Linux from the scratch to the advance.
What is Netcat
Netcat aka nc is a network utility for reading from and writing to network connections using TCP and UDP. Netcat is very useful to both attacks and the network security auditors.
For an attacking purpose it is a multi-functional tool which accurate and useful. Security auditors uses Netcat to debug and investigate the network.
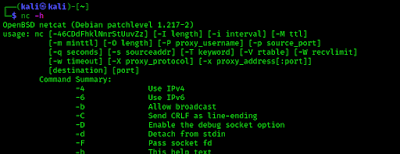
To start with netcat we just check the help section of netcat by using following command:
The following screenshot shows the output of preceding command:
Port Scanning with Netcat
Netcat can be used as a port scanner. Netcat is not created for port scanning, but if we use -z flag then we are able to do it. -z flag used to scan listing daemon without sending any data. This makes it possible to understand the type of service that is running on that specific port. Netcat can perform both TCP and UDP scan.
TCP Scan with Netcat
To scan a target machine we run following command:
Here we have used some flags, -v flag is used for verbose mode, -n indicates numeric-only IP address and -z indicates zero -I/O model (basically used for scanning).
We also need to specify a range of ports (10 to 400) and we get the result as shown in the following screenshot:
UDP Scan with Netcat
We also can scan the UDP ports using Netcat. With the help of following command we have scanned UDP port using netcat.
Here we have used -u flag for scanning UDP ports, as seen in the following screenshot:
Chatting with Netcat
Two users can chat through netcat. But before that they need to establish connection. To set all this we gonna use two different devices. One OS is Elementary OS and another is our fab Kali. To set up the connection we need to know the IP address of systems (In our case we are using local IP).
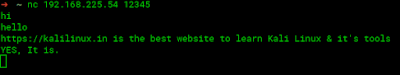
From a device we can start the initiator. We run following command from our Elementary OS to start initiator:
Here the IP address is our Elementary OS's local IP address and we have chosen port number 12345 for just an example. As we can see in the following screenshot:
Now from our Kali Linux we use following command to start listener.Here -l flag used for listen mode, v is used for verbose mode and p is used for local port.
Now the connection has been setup and both system are capable to communicate to each other.
Where we are not in our local network we can use our external IP in the place of local IP and forward our selected port on initiator system.
Banner Grabbing using Netcat
Banner grabbing is collection of information from the host machine. We also can do it using netcat. We run following command to see information of services running on a specific port:
In the following screenshot we can see version of running services on the port.
File Transfer via Netcat
Netcat also offers an ability to transfer or share files from on device to other device. This is quite similar process of sending texts.
We have a text file named file.txt on our Kali Linux system, to share it we use following command:
The following screenshot shows that shearing is started.
Now we can downloaded it from another system. Here for an example we have used Termux terminal from our android device. From other device we need to run following command to save the file. Here we need the IP address of our Kali Linux machine (we are using local IP).
We can see it on the following screenshots:
The above display shows the output of Kali Linux and the lower part of above screenshot shows the fie we have received on our android device using Netcat.Reverse Shell using Netcat
Everyone knows that netcat have a major role to exploit target machines. This is very helpful for CTF players and bounty hunters. This also works with Metasploit payloads.
Linux Reverse Shell
We can easily create a reverse shell with the help of "msfvenom" and setup the listener using netcat. For a Linux system as target we can use following command:
Here we used R flag used to generate a raw payload (Just the command).
After creating the payload we can just need to run it to target machine but before that we start a netcat listener on attacker machine by by using following command:
Whenever the target runs the payload we'll get the session. We can see that in the following screenshot:
Sometimes for security reason we might not get the session using above method. In that case we can start netcat listener on 443 port using following command:
Then we just need to execute following commands on target Linux machine:
BANG! We got shell!
Windows Reverse Connection
We can get target windows system's command prompt on attacker machine easily.
To do that we just need to start the listener on attacker machine (Kali Linux) by applying following command:
On the target Windows system we just need to run following command on command prompt (Windows CMD):
Just after that we can easily get the command prompt of the target machine on our attacker terminal. As we can see in the following screenshot:
If we need to create a payload in .exe file then we need to create a "msfvenom" payload by applying following command:
This command will create a shell.exe file. If the target Windows system runs the exe file then we got the shell by opening listener on that specific port.
We also can create persistence backdoor on Windows using Netcat.
Netcat is very important for cybersecurity experts and bug bounty hunters. We can do almost anything using Netcat. We hope we got a clear idea on Netcat and it's uses on Kali Linux.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.