In this digital forensic tutorial we are going to learn how to reset forgotten password of Windows 7 or Windows 8 or Windows 10. Using this forensic method we can unlock any Windows devices without knowing the user password and without formatting the hard disk.
Suppose we work in a digital forensic lab and we got a crime case with a locked Windows computer. We have to unlock it to collect evidence. This method also work for anyone who forgot password of a Windows computer.
To perform this forensic experiment we use a little program called chntpw. This chntpw can change password of a user in Windows SAM files, even this program can edit Windows registry. This free forensic tool comes pre-installed in Kali Linux.
Here suppose we got a locked Windows laptop running Windows 8, and we don't know the password. Now we have to change/reset the password to get administrative access in this laptop. To do this we need a live USB installed Kali Linux on our pen drive. Now how to do this ? Making a live bootable USB of Kali Linux is very easy follow this tutorial.
Now we need to open the BIOS settings on the locked computer and plug our USB pen drive where we have our Kali Linux installed and boot the PC from external removable USB devices. We got this on the boot menu on BIOS settings.
This process depending on the motherboard.
Here we boot Kali Linux as live boot.
After boot we can see Kali Linux on the PC and we can use any tool of Kali Linux now.
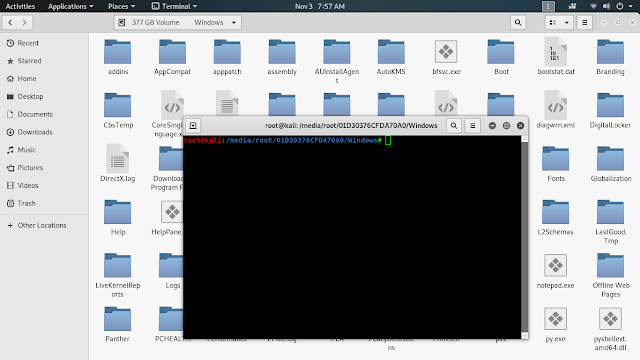
So we have booted live Kali Linux in the locked Windows pc. Now we open file manager go to the Windows hard disk as shown in following:
Here we go in to the Windows folder, and then open terminal there by right click.
To reset the password we need to configure SAM files located in System32/config/ . So our command will be following:
Then we check for the SAM files by using ls command:
The screenshot is following:
Here we are going to changes on SAM files. Before do it we can back-up the SAM files. If anything goes wrong then we have the back up files to restore as previous.
Now we check the options of chntpw by using following command:
The screenshot of the command is following:
First we use the -l flag to see all the users in the SAM file:
We can see the list of users in the following screenshot:
Using chntpw tool tool we can make any user to admin user bat for now we change the password of KPAL user.
Now we use following command to change anything on KPAL user:
Then the user edit menu will appear in front of us as following screenshot:
Here we can see in the screenshot we got some option.
Here we will choose option 1 to clear the password and hit enter the screenshot is following:Suppose we work in a digital forensic lab and we got a crime case with a locked Windows computer. We have to unlock it to collect evidence. This method also work for anyone who forgot password of a Windows computer.
To perform this forensic experiment we use a little program called chntpw. This chntpw can change password of a user in Windows SAM files, even this program can edit Windows registry. This free forensic tool comes pre-installed in Kali Linux.
Here suppose we got a locked Windows laptop running Windows 8, and we don't know the password. Now we have to change/reset the password to get administrative access in this laptop. To do this we need a live USB installed Kali Linux on our pen drive. Now how to do this ? Making a live bootable USB of Kali Linux is very easy follow this tutorial.
Now we need to open the BIOS settings on the locked computer and plug our USB pen drive where we have our Kali Linux installed and boot the PC from external removable USB devices. We got this on the boot menu on BIOS settings.
This process depending on the motherboard.
Here we boot Kali Linux as live boot.
After boot we can see Kali Linux on the PC and we can use any tool of Kali Linux now.
So we have booted live Kali Linux in the locked Windows pc. Now we open file manager go to the Windows hard disk as shown in following:
 | |
| The 377GB Volume is our Windows Drive (This will be not same for everyone) |
To reset the password we need to configure SAM files located in System32/config/ . So our command will be following:
Then we check for the SAM files by using ls command:
The screenshot is following:
Here we are going to changes on SAM files. Before do it we can back-up the SAM files. If anything goes wrong then we have the back up files to restore as previous.
Now we check the options of chntpw by using following command:
The screenshot of the command is following:
First we use the -l flag to see all the users in the SAM file:
We can see the list of users in the following screenshot:
Using chntpw tool tool we can make any user to admin user bat for now we change the password of KPAL user.
Now we use following command to change anything on KPAL user:
Then the user edit menu will appear in front of us as following screenshot:
Here we can see in the screenshot we got some option.
- Option 1 will clear the password of selected user.
- Option 2 will unlock or enable a disabled user account.
- Option 3 will promote the selected user to admin user.
- Option 4 will add selected user in a group.
- Option 5 will remove selected user from a group.
- Option q is for quit.
Now we need to save and quit this. For this we type q and press Enter for quit then chntpw will prompt if we wan't to save these files or not ? Here we hit y for yes and press enter as the following screenshot :
Now we can log in the Windows user without password.
Now we can turn off the system and remove the USB bootable Kali Linux.
Then we change the BIOS boot menu to boot it from hard disk. Means we revert the changes in BIOS. Then we boot as normal and we do not need password to log in as KPAL user.
So here we have learned successfully removed password of this Windows and we can collect all information. We can assign a new password to change password if we wish. This is a very easy task and a must know for every penetration testers and digital forensic experts. By this method we can change or remove password of any Windows.