A company or organization may have some hidden sub-domains not listed in search engines. This type of sub-domains may have vulnerabilities. In this tutorial we learn how to find hidden and internal sub-domains using ct-exposer.
Certificate Transparency (CT) is an internal security standard and open source framework for auditing and monitoring digital certificates. This standard creates a system of public logs that seek to eventually record all certificates issued by publicly trusted certificate authorities, allowing efficient identification of mistakenly or maliciously issued certificates.
Certificate transparency logs maintain records of issued Secure Sockets Layer (SSL) certificates. These logs are append-only, that means, entries in this log can not be deleted or altered anyway. This is for stopping misuse of certificates.
Ct-exposer is a python based tool it uses ct-logs to display results of providing website, then it will try to do DNS look ups for the sub-domains to check the sub-domains are exists in DNS or not.
Domains without DNS record may be old/expired domains or may be internal only domains. Internal only domains can be resolves in internal server only.
For a security expert or a bug-bounty hunter ct-exposer is a grate tool because it finds all sub-domains lists. Some sub-domains may have lower security.
Let's see how we can use ct-exposer in our Kali Linux system. Ct-exposer is not comes with Kali Linux. We need to clone it from it's Github repository. To do this we open the terminal window and apply following command :
The screenshot is following:
Now we need to go into ct-exposer's folder by using following command :
Then we check for files using ls command. In the following screenshot we can see the main python script.
Before running the python script we install requirement packages for this framework. To do this we run the following command:
Then it will install requirement packages listed in requirements.txt file, as like the following screenshot:
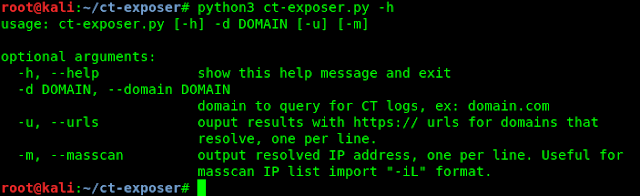
Now we can run this tool. First we check the help to know which options are available in ct-exposer tool. To open the help of ct-exposer we apply following command:
We can see the options like following screenshot:
We can use -d for domain and -u for url and -m for mass scan.
Let's find out the sub-domains using ct-logs.
Here in this tutorial for an example we hunt for Google's hidden sub-domains using following command:
Then it will download the list of domains and show us like following screenshot:
We did it we found the sub-domains list from ct-logs.
Here in the above screenshot we got two lists:
DNS recorded domains are public domains that means we can open them in our browser. There may be some low secured domains.Certificate Transparency (CT) is an internal security standard and open source framework for auditing and monitoring digital certificates. This standard creates a system of public logs that seek to eventually record all certificates issued by publicly trusted certificate authorities, allowing efficient identification of mistakenly or maliciously issued certificates.
Certificate transparency logs maintain records of issued Secure Sockets Layer (SSL) certificates. These logs are append-only, that means, entries in this log can not be deleted or altered anyway. This is for stopping misuse of certificates.
Ct-exposer is a python based tool it uses ct-logs to display results of providing website, then it will try to do DNS look ups for the sub-domains to check the sub-domains are exists in DNS or not.
Domains without DNS record may be old/expired domains or may be internal only domains. Internal only domains can be resolves in internal server only.
For a security expert or a bug-bounty hunter ct-exposer is a grate tool because it finds all sub-domains lists. Some sub-domains may have lower security.
Let's see how we can use ct-exposer in our Kali Linux system. Ct-exposer is not comes with Kali Linux. We need to clone it from it's Github repository. To do this we open the terminal window and apply following command :
The screenshot is following:
Now we need to go into ct-exposer's folder by using following command :
Then we check for files using ls command. In the following screenshot we can see the main python script.
Before running the python script we install requirement packages for this framework. To do this we run the following command:
Then it will install requirement packages listed in requirements.txt file, as like the following screenshot:
Now we can run this tool. First we check the help to know which options are available in ct-exposer tool. To open the help of ct-exposer we apply following command:
We can see the options like following screenshot:
We can use -d for domain and -u for url and -m for mass scan.
Let's find out the sub-domains using ct-logs.
Here in this tutorial for an example we hunt for Google's hidden sub-domains using following command:
Then it will download the list of domains and show us like following screenshot:
We did it we found the sub-domains list from ct-logs.
Here in the above screenshot we got two lists:
- Domains with DNS record.
- Domains with no DNS record.
Domains with no DNS record is may be old/not using now domains or internal only domains. Internal only domains can be accessible only in own internal server.
This is how ct-exposer works. It is very easy, isn't it?